How can I make SSH more secure?
Posted: Tue May 17, 2022 11:53 pm
SSH or Secure Shell, sometimes also known as Secure Socket Shell, is the protocol (software) you use when you connect to your server using PuTTY or even WinSCP.
When you connect to your server using SSH locally (on the same network), there is no need to have SSH set up for port forwarding on your router.
This means that any device that is beyond your router (out there in internet land) won’t be able to connect using SSH as they will not be able to get past your router and therefore not reach your server.
The problem is that if you activate port forwarding for SSH, on the standard port of 22, lots of idiot hackers will try their luck at logging in.
If you do have SSH port forwarding on your router you will most likely get multiple reports from Fail2ban telling you it has blocked these idiots IP addresses.
So, it is fine not to have it activated on your router, however if you need to log in using SSH when you are away from home, you will not be able to, for the reason I described above.
So how do we get around this?
Ok, so as long as you know what port number to use when you connect, there is no reason we have to use port 22.
The chances are the hackers will not know which port number you have used, so there is less chance of being hacked into.
This is not a perfect solution, however if you change the port number regularly, and turn SSH port forwarding off on your router (when you don’t need it on), you will significantly lower the risk of getting hacked.
Ok, I hope you are still with me.
By default, your server listens for an incoming SSH connection on port 22, so we would first need to change that to another port number.
The port number range we have to choose from is vast as it is between 1024 and 65535, so this makes it harder for your port number to be discovered.
Ok so let’s pick a random number within that range, so for my example I have picked port number 2754, you would be better to choose a different number, for better security (as this one is published on this public website).
Changing it on your server is a relatively simple task, so let’s get started.
Log into your server using your PC and PuTTY.
Issue this command.
sudo vi /lib/systemd/system/ssh.socket
scroll down to this line (should be about line 7).
ListenStream=22
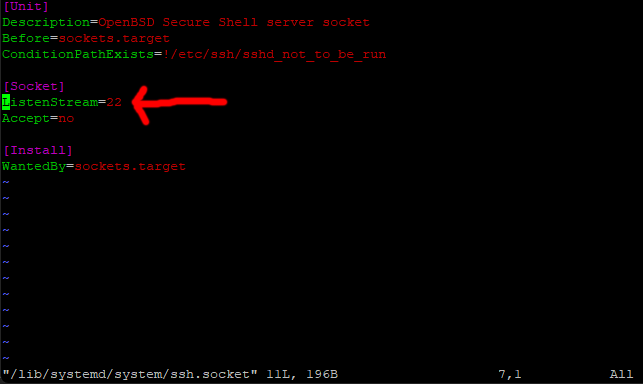
Now before we go any further, it is important you use a number you can remember, and double check you have typed it correctly.
Press I for insert, then change the 22 to the port number you are going to use.
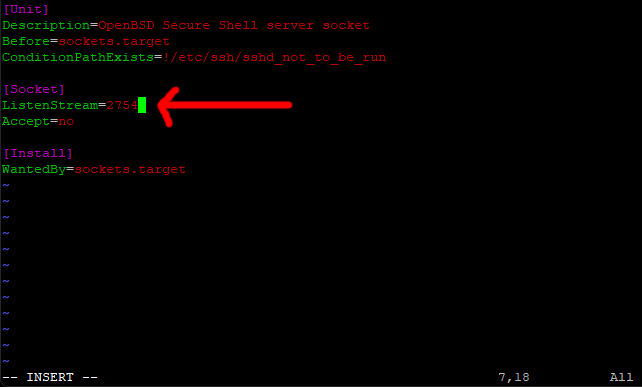
Save and exit (escape :w (enter) :q (enter))
Be aware that once the server has re-booted you will no longer be able to connect using the PuTTY default port of 22.
Ok, When ready issue the reboot command.
sudo shutdown -r now
Ok, for testing try to log back in with PuTTY with the default port.
If all has gone to plan, you should see an error similar to this.
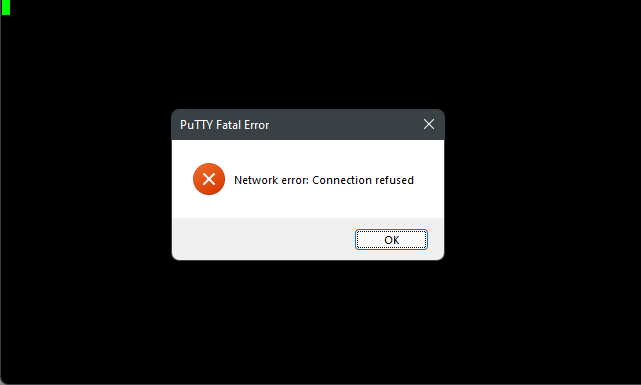
Ok, open PuTTY again, this time change the port number, to the one you set up.
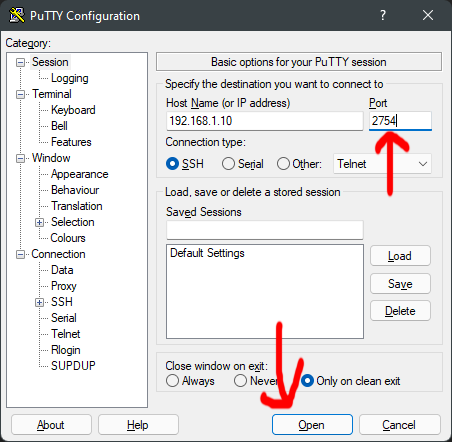
Now, try to log in.
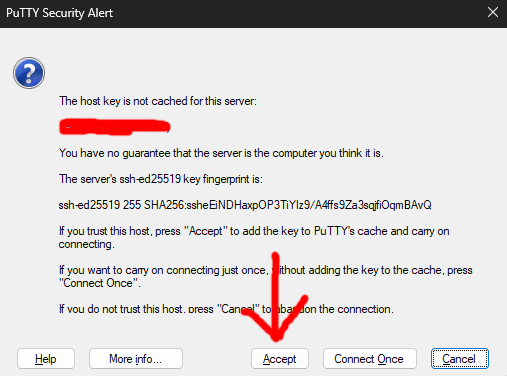
You may see the standard PuTTY security alert screen, just click Accept.
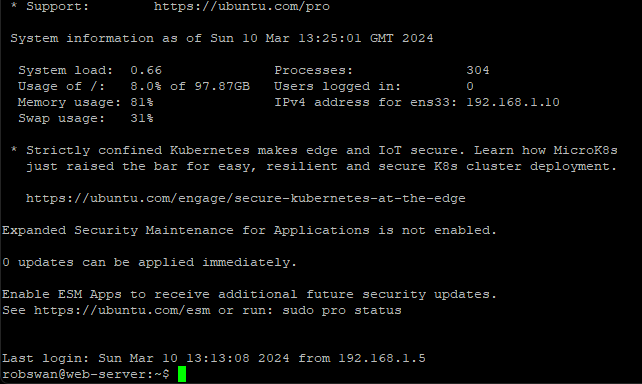
You should find you are now logged back in.
Ok, that’s the port number changed on your server.
You can close PuTTY by entering the command exit.
Remember whenever you log into your server using SSH, be it with PuTTY or even WinSCP you will need to use the new port number.
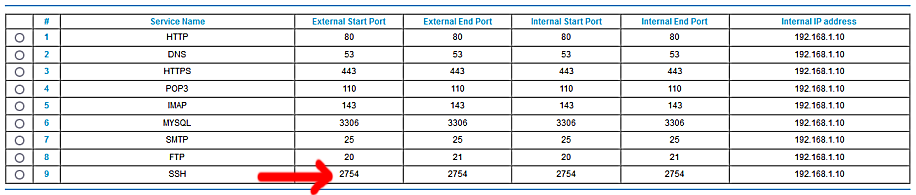
So, when your away from home, you can turn port forwarding on for SSH (on your router), but use your new port number, so on a Netgear router as per our example it would look like this.
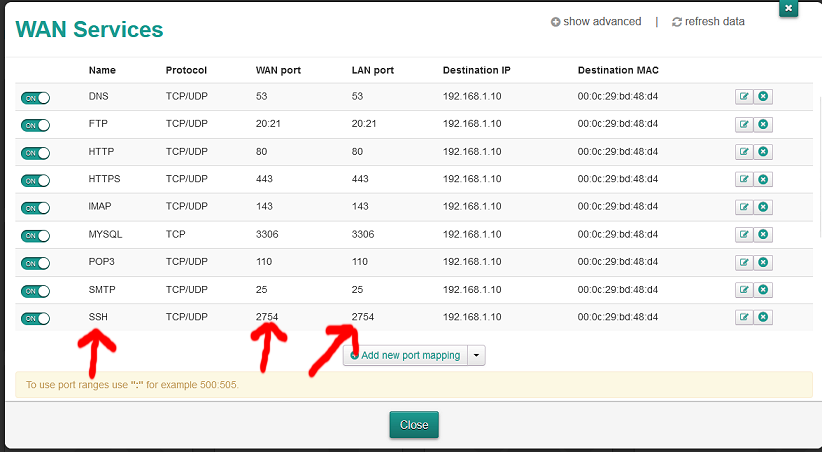
If you use a Technicolor router it would look like this.
One final point, if you forget the port number, you would have to log into your actual physical server to reset it (using the method above).
We are all done here.
When you connect to your server using SSH locally (on the same network), there is no need to have SSH set up for port forwarding on your router.
This means that any device that is beyond your router (out there in internet land) won’t be able to connect using SSH as they will not be able to get past your router and therefore not reach your server.
The problem is that if you activate port forwarding for SSH, on the standard port of 22, lots of idiot hackers will try their luck at logging in.
If you do have SSH port forwarding on your router you will most likely get multiple reports from Fail2ban telling you it has blocked these idiots IP addresses.
So, it is fine not to have it activated on your router, however if you need to log in using SSH when you are away from home, you will not be able to, for the reason I described above.
So how do we get around this?
Ok, so as long as you know what port number to use when you connect, there is no reason we have to use port 22.
The chances are the hackers will not know which port number you have used, so there is less chance of being hacked into.
This is not a perfect solution, however if you change the port number regularly, and turn SSH port forwarding off on your router (when you don’t need it on), you will significantly lower the risk of getting hacked.
Ok, I hope you are still with me.
By default, your server listens for an incoming SSH connection on port 22, so we would first need to change that to another port number.
The port number range we have to choose from is vast as it is between 1024 and 65535, so this makes it harder for your port number to be discovered.
Ok so let’s pick a random number within that range, so for my example I have picked port number 2754, you would be better to choose a different number, for better security (as this one is published on this public website).
Changing it on your server is a relatively simple task, so let’s get started.
Log into your server using your PC and PuTTY.
Issue this command.
sudo vi /lib/systemd/system/ssh.socket
scroll down to this line (should be about line 7).
ListenStream=22

Now before we go any further, it is important you use a number you can remember, and double check you have typed it correctly.
Press I for insert, then change the 22 to the port number you are going to use.

Save and exit (escape :w (enter) :q (enter))
Be aware that once the server has re-booted you will no longer be able to connect using the PuTTY default port of 22.
Ok, When ready issue the reboot command.
sudo shutdown -r now
Ok, for testing try to log back in with PuTTY with the default port.
If all has gone to plan, you should see an error similar to this.

Ok, open PuTTY again, this time change the port number, to the one you set up.

Now, try to log in.
You may see the standard PuTTY security alert screen, just click Accept.

You should find you are now logged back in.

Ok, that’s the port number changed on your server.
You can close PuTTY by entering the command exit.
Remember whenever you log into your server using SSH, be it with PuTTY or even WinSCP you will need to use the new port number.
So, when your away from home, you can turn port forwarding on for SSH (on your router), but use your new port number, so on a Netgear router as per our example it would look like this.

If you use a Technicolor router it would look like this.

One final point, if you forget the port number, you would have to log into your actual physical server to reset it (using the method above).
We are all done here.