Making the changes to Fail2ban in this topic will, increase your server security, by making it less likely your server will get hacked into by some idiot.
Please be aware that no system security is ever perfect, but in my opinion it is better to reduce that risk a bit, anyway it is you call.
This topic is quite a complicated process, so if you opt to do this, make sure you have plenty of time.
To make it a bit easier, I have broken it down into bite size chunks as follows.
1. Create Some Cron Jobs.
2. Activate Some New Log Files.
3. New Logrotate Settings.
4. New Configuration Settings For Fail2ban.
5. Fail2ban Basic Operations (How To Use).
There is no reason why you cannot take a break between each section!
Ok, let’s get started with part 1.
1. Create Some Cron Jobs.
Connect to your server using PuTTY and your PC.
Issue this command.
sudo crontab -e
Please note your file may look different to the one in the example.
As always when adding new lines at the bottom, move the cursor to the last letter of the last line, press I for insert, move the cursor one place to the right (so its just after the last letter) and then press enter for a new line.
Paste these lines in (right click on the cursor to paste).
Code: Select all
# Fail2ban: MySQL/RC/SM Log File Permission Settings
@reboot /bin/chmod -R 2750 /var/log/mysql/ >/dev/null 2>&1
@reboot /bin/chgrp adm /var/log/mysql/ >/dev/null 2>&1
@reboot /bin/chown -R www-data:www-data /var/log/roundcube/ >/dev/null 2>&1
@reboot /bin/chmod -R 775 /var/log/roundcube/ >/dev/null 2>&1
@reboot /bin/chmod 777 /var/log/squirrelmail.log >/dev/null 2>&1
@reboot /usr/sbin/service mysqld restart >/dev/null 2>&1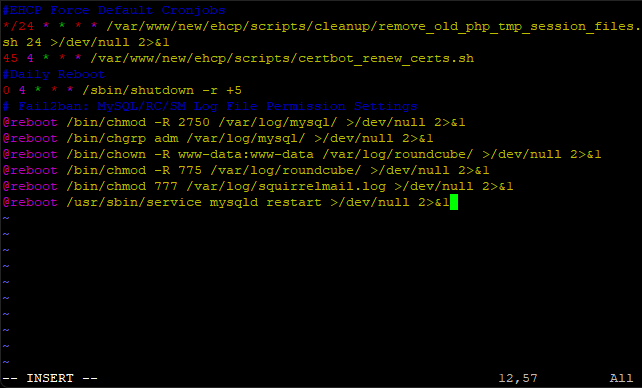
Save and exit (Escape :w (enter) :q (enter)).
Ok, some might think the above is massive overkill, however I have done extensive testing and it is the best method.
So, what have we done?
We have given read write permissions to the logs files we need to be working. Ubuntu server has a nasty habit of resetting permissions, so we have set it to do this each time the server reboots. This will make sure that we never have a problem with the log files.
2. Activate Some New Log Files.
Fail2ban watches log files to check for failed log in attempts by potential hackers, most of the applications on your server log these things already, but unfortunately three of them do not.
Hackers are well aware that most people will not have these applications monitored by Fail2ban so they may choice to use them as a possible way in.
The three applications that we need to change are Roundcube (your main online email client), MySQL and Squirrelmail (the alternative email client that is on your server).
We will start with Roundcube first.
EHCP force does provide a folder for the Roundcube log files, but by default logging it turned off.
The first thing we need to do is make the folder writable.
Issue these commands in Putty to set the permissions now, so we don’t have to reboot the server.
sudo chown -R www-data:www-data /var/log/roundcube/
sudo chmod -R 775 /var/log/roundcube/
Ok so now we need to turn on logging in Roundcube.
So, staying in Putty issue this command.
sudo vi /etc/roundcube/config.inc.php
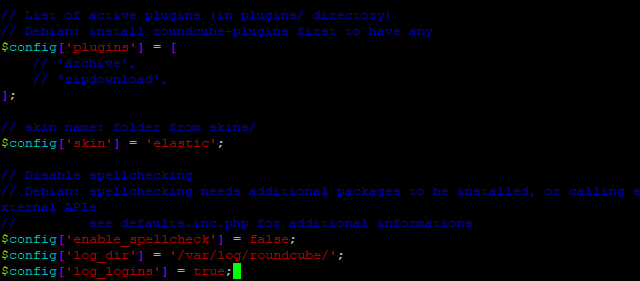
Scroll down to the end of the file, Press I for insert and put in these lines.
$config['log_dir'] = '/var/log/roundcube/';
$config['log_logins'] = true;
So the end of the Roundcube configuration file should look a bit like this.
Save the changes and exit the editor (Esc, :w (enter), :q(enter))
If is really important that we make Roundcube create the error log file, to do this go to Roundcube webmail, (Mail.YourDomain.com) and just once, attempt to login using nonsense.
Next, we need to clear this out of the log, as this was just us and not a hacker.
Issue this command.
sudo vi /var/log/roundcube/errors.log
Then, to empty the file type :%d like this.
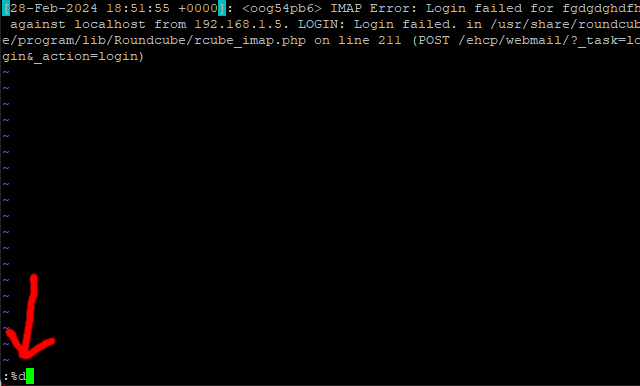
Press enter.

Ok Save and exit the editor in the normal way :w (Enter), :q (Enter).
So that should be Roundcube sorted!
The next one to sort is MySQL.
If you followed the topic called “Essential command line configuration to be done next“ all the way through then MySQL Should already be sorted, if you did not then go back and follow it!
So that is MySQL sorted!
Next we need to do Squirrelmail which is a bit more complicated.
First change into root user mode using this command.
sudo su
Next, enter this command.
cd /var/www/new/ehcp/webmail2/plugins
We need to download a plugging for Squirrelmail so use this command.
wget -O "squirrel_logger-2.3.1-1.2.7.tar.gz" -N http://squirrelmail.org/countdl.php?fileurl=http%3A%2F%2Fwww.squirrelmail.org%2Fplugins%2Fsquirrel_logger-2.3.1-1.2.7.tar.gz
Next we need to unzip the file we have just downloaded so issue this command.
tar zxvf squirrel_logger-2.3.1-1.2.7.tar.gz
Then this.
cd squirrel_logger
Now this
cp config_example.php config.php
Ok we now need to create a log file for Squirrelmail to write to, so use these commands to achieve this.
touch /var/log/squirrelmail.log
chown www-data:www-data /var/log/squirrelmail.log
chmod 777 /var/log/squirrelmail.log
Now we need to tell Squirrelmail which file to write to, so we need this command to edit a configuration file.
vi config.php
Scroll down until you see this line (should be about line 313).
$sl_logfile = $data_dir . 'squirrelmail_access_log';
Press I for insert and change the line to this.
$sl_logfile = '/var/log/squirrelmail.log';
So that part of the configuration file should look a bit like this.
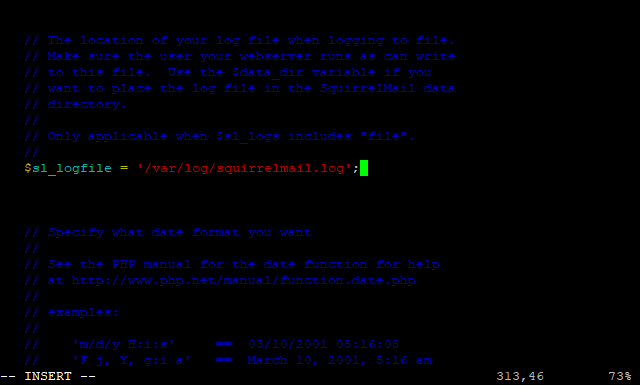
Next save the changes and exit the editor (Esc, :w (enter) :q (enter)
Ok next issue these two commands to delete the original zipped file we downloaded.
cd ..
rm squirrel_logger-2.3.1-1.2.7.tar.gz
Now we need to actually turn the logging to file for Squirrelmail on.
Squirrelmail has a built in settings utility which makes this a relatively easy task.
To access this utility use these commands.
cd ..
cd config
./conf.pl
When the utility loads you will be faced with a list of options.
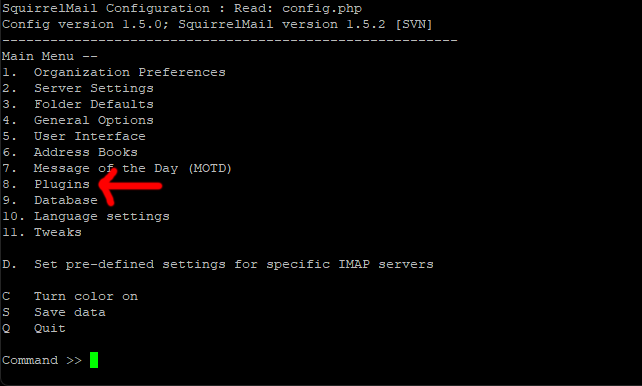
Ok, type the number which is for plugins (normally number 8) then press enter.
On the next screen type the number that corresponds to squirrel_logger in my case this was 16 (press enter).
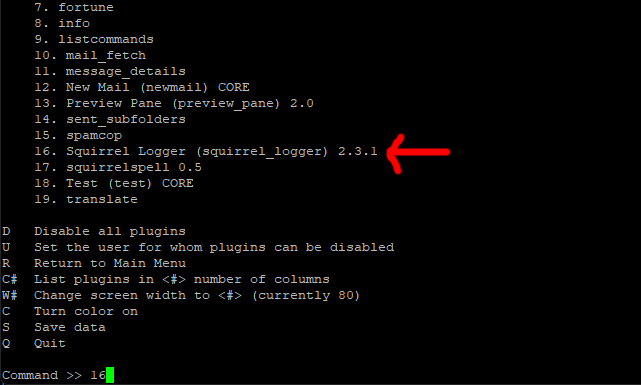
Finally just type S to save the data (enter) (enter), and then Q for quit (Enter)
Move back out of root user mode by entering the command.
exit
IMPORTANT NOTES: -
Setting the Squirrel mail log file permissions to 777, does not in any way represent a security risk.
When updating EHCP force you MUST use the script in THIS POST, or the work we have done to enable the Squirrel logger will be undone.
Ok, that should be Squirrelmail set up for logging.
This may be a good time to take a break as we still have a lot to do but it’s safe to take a break at this point.
3. New Logrotate Settings.
It’s a good idea to add the new Squirrelmail log file to Logrotate.
Logrotate is basically an application on your server that stops log files getting too large as it cleans them out periodically.
Thankfully this is a relatively simple task.
So, staying with PuTTY, issue this command.
sudo vi /etc/logrotate.d/Squirrelmail
Press I for insert and paste in this code.
Code: Select all
/var/log/squirrelmail.log
{
su www-data www-data
create 0777 www-data www-data
compress
delaycompress
missingok
notifempty
rotate 5
weekly
}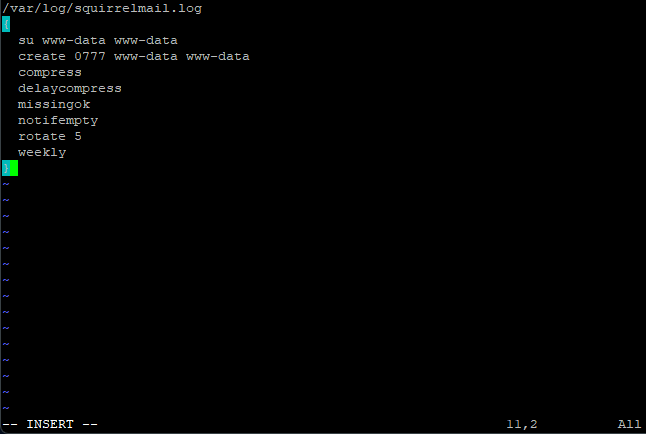
Save and exit (escape :w (enter) :q (enter))
Yes, that is it done for Squirrelmail.
Ok, MySQL has already got settings in Logrotate, so no action is needed.
Next, Roundcube has a configuration in Logrotate, we just need a slight edit of the config file.
So, issue this command.
sudo vi /etc/logrotate.d/roundcube-core
move, the cursor (using the arrow key) to the first letter of the line create 0640 www-data adm.
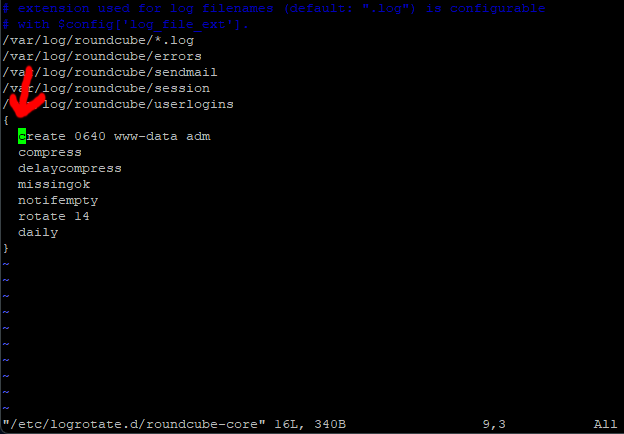
Press I for insert, then press enter to create a new line above.
You may notice that the line (create 0640 www-data adm) has moved all the way to the left.
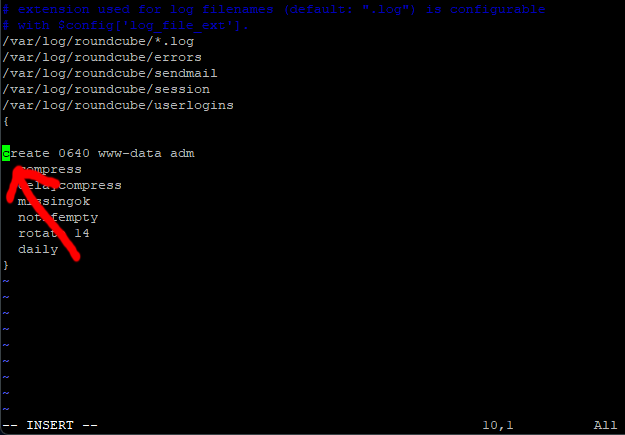
Fix this, by pressing space twice.
Next, move the cursor up to the new empty line above.
Your, cursor should stay lined up with the line underneath.
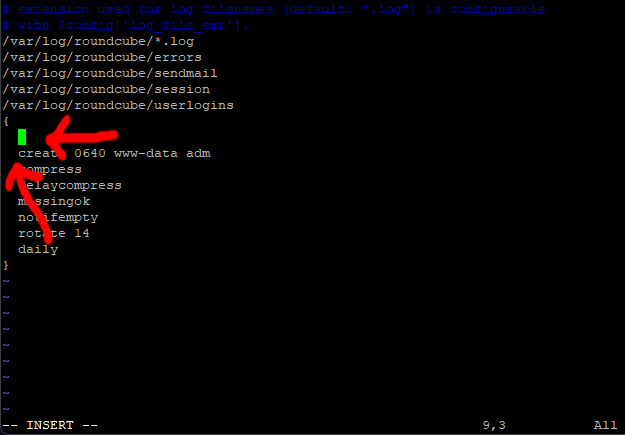
Paste this line in.
su www-data www-data
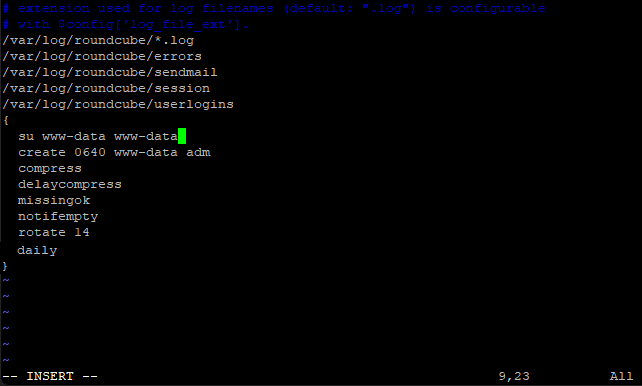
Next, on the line underneath change 0640 to 0775 and adm to www-data.
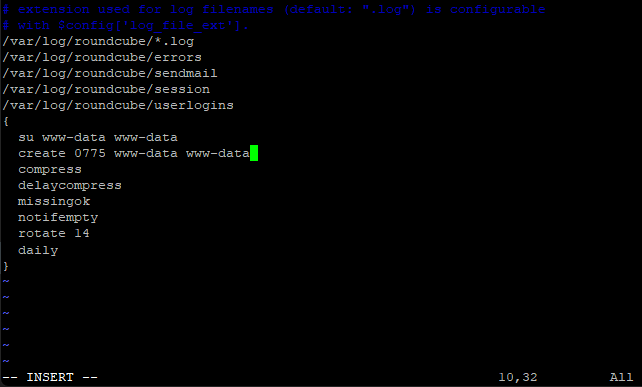
Next go to the line that says rotate 14, change 14 to 5.
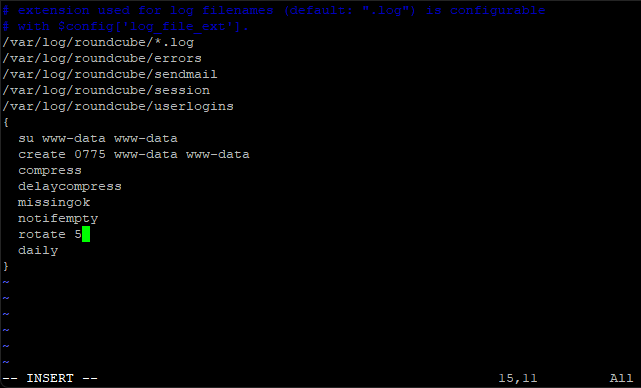
Finally (line underneath) change daily to weekly.
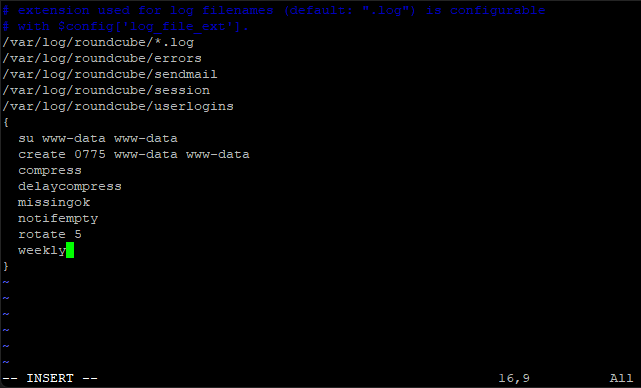
Save and exit (escape :w (enter) :q (enter))
We are now done with Logrotate.
4. New Configuration Settings For Fail2ban.
Ok, so now its time for the tricky bit.
As you will probably know, Fail2ban blocks suspicious IP addresses from your server.
Each potential entry point is called a Jail.
So, for example if someone tries to log into Roundcube webmail and has a set number of failed attempts, Fail2ban will automatically ban them from accessing your server.
There IP address will be stored in the Roundcube Jail within Fail2ban, they will only be un-banned when either you tell Fail2ban to do so, or a set amount of time has passed.
We control how many failed attempts result in a ban, and how long an IP address should remain banned for.
As a general rule I recommend setting the ban time for 1 year, and the number of failed attempts that result in a ban as 5.
We can also stop Fail2ban blocking us by telling it to ignore certain IP Addresses.
We can see how many jails Fail2ban is currency running using this command in PuTTY.
sudo fail2ban-client status
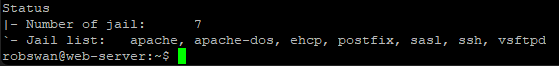
As you can see, we are currency running 7 jails, this is not enough in my opinion.
Most of the settings for Fail2ban are stored in the file jail.local in the folder /etc/fail2ban/.
Let get started then, so issue this command to edit the main setting file for Fail2ban.
sudo vi /etc/fail2ban/jail.local
The first thing we are going to look at is the ignore IP setting.
Move to the line that says ignoreip = 127.0.0.1 (about line number 21).
Place the cursor at the end of the line, press I for insert, move on place to the right, next press space.
Type your routers local IP Address (usually 192.168.1.1), then space, then your public IP address (the one from your ISP), its space again and finally the local IP address of the main PC that you use to access your server.
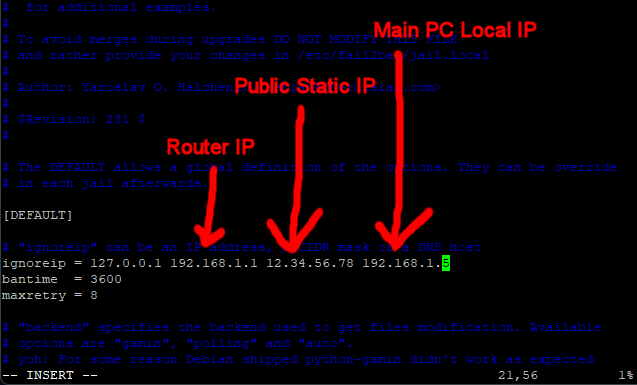
You can add as many IP addresses as you want to this line (separated by a space).
As the line suggests, these are the IP addresses that Fail2ban will ignore.
Scroll down to the next line (bantime) and change it to 525600m (1 year), this is how long in minutes we want to ban someone.
Now scroll down one more line and change the maxretry to 5 (this is how meny failed attempt to allow before someone is banned).
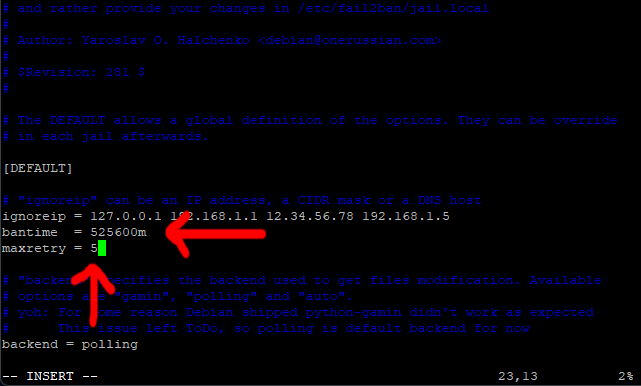
Next, move your cursor the beginning of the line under maxretry = 5 (no need to add a new line).
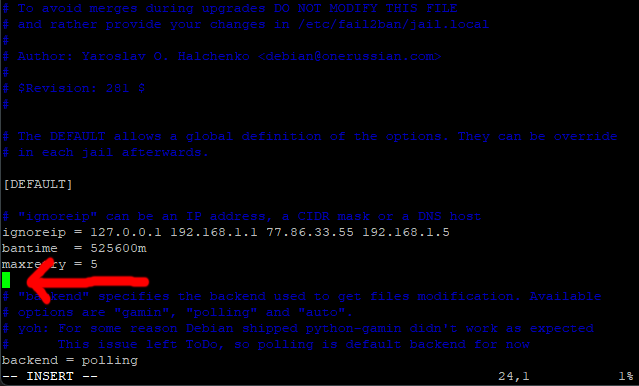
Paste in this line.
findtime = 1440m
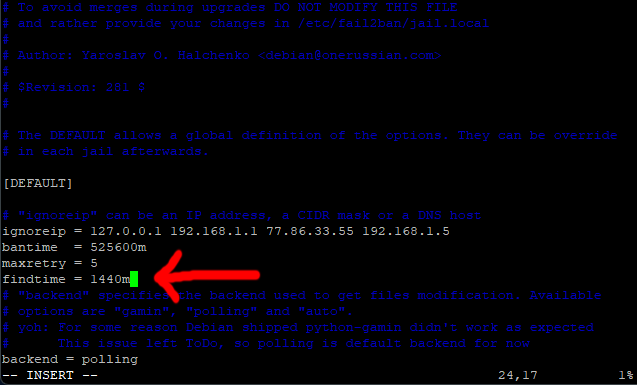
Find time is the length of time Fail2ban, counts failed attempts from an IP address.
As there are 1440 minutes in 24 hours, we telling Fail2ban to ban anybody with 5 failed attempts within a 24 hour period for 1 year.
These are the default settings, they can be overridden within an individual jail (if you feel the need).
You can if you wish, change the above stettings to whatever you want, however these are the settings I personally recommend.
Before we change anything else we are going to apply these settings so save and exit (escape :w (enter) :q (enter))
Issue this command to restart Fail2ban.
sudo fail2ban-client restart
If all is good with our new settings you should see Server Ready.

Now, please reopen the file with the same command.
sudo vi /etc/fail2ban/jail.local
You can apply new settings, as often as you want (as above).
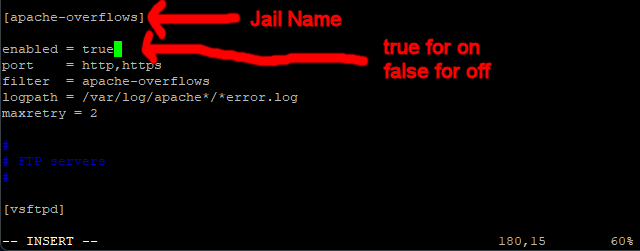
Scroll down to the line that says [apache-overflows] (should be about line 216)
This is the section for a jail called [apache-overflows]
Now, we are going to turn this jail on.
So scroll down 2 lines, to the line that says enabled = false
Press I for insert, and change false to true.
Scroll Down to the bottom of the file and add this code.
Making sure you start on a new line of course.
Code: Select all
#Extra Jails Not Listed By Default---------------------------------------------
#apache
[apache-auth]
enabled = true
port = http,https
logpath = %(apache_error_log)s
[apache-badbots]
# Ban hosts which agent identifies spammer robots crawling the web
# for email addresses. The mail outputs are buffered.
enabled = true
port = http,https
logpath = %(apache_access_log)s
bantime = 48h
maxretry = 1
[apache-botsearch]
enabled = true
port = http,https
logpath = %(apache_error_log)s
maxretry = 2
[apache-fakegooglebot]
enabled = true
port = http,https
logpath = %(apache_access_log)s
maxretry = 1
ignorecommand = %(fail2ban_confpath)s/filter.d/ignorecommands/apache-fakegooglebot <ip>
[apache-modsecurity]
enabled = true
port = http,https
logpath = %(apache_error_log)s
maxretry = 2
[apache-shellshock]
enabled = true
port = http,https
logpath = %(apache_error_log)s
maxretry = 1
[apache-nohome]
enabled = true
port = http,https
logpath = %(apache_error_log)s
maxretry = 2
#------------------------------
#Webmail
[roundcube-auth]
enabled = true
port = http,https
logpath = /var/log/roundcube/errors.log
[squirrelmail]
enabled = true
port = smtp,465,submission,imap,imap2,imaps,pop3,pop3s,http,https,socks
logpath = /var/log/squirrelmail.log
#------------------------------
#MySQL
[mysqld-auth]
enabled = true
port = 3306
logpath = /var/log/mysql/mysql.log
backend = %(mysql_backend)s
#------------------------------
#PHPMyAdmin
[phpmyadmin-syslog]
enabled = true
port = http,https
logpath = %(syslog_authpriv)s
backend = %(syslog_backend)s
#------------------------------
#Sendmail
[sendmail-auth]
enabled = true
port = submission,465,smtp
logpath = %(syslog_mail)s
backend = %(syslog_backend)s
[sendmail-reject]
enabled = true
port = smtp,465,submission
logpath = %(syslog_mail)s
backend = %(syslog_backend)s
#End---------------------------------------------------------------------------
Issue this command to restart Fail2ban.
sudo fail2ban-client restart
Again, if all is good with our new settings you should see Server Ready.

Now, let’s issue this command to see our new Jails and configuration in all of their glory.
sudo fail2ban-client status
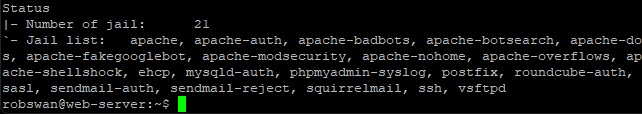
Ok, that is Fail2ban (Finally) sorted.
5. Fail2ban Basic Operations (How To Use).
Every time Fail2ban actually bans someone it will send you an email to the email address we set up in THIS POST, don’t be alarmed if you start getting a lot of these emails, as most servers get spotted very quickly by hackers.
The email can give you a lot of detail about the offending IP address.
If the unusual event that you wish to unban someone it can be done from a single command in Putty.
Ok, here is how to unban someone.
First of all examine the email that informed you of the ban, you need the IP address and the jail name in order to unban it.
Here is an example, so you get the idea.
So let’s open one of these emails, and look at the information at the top.
This is one of mine.
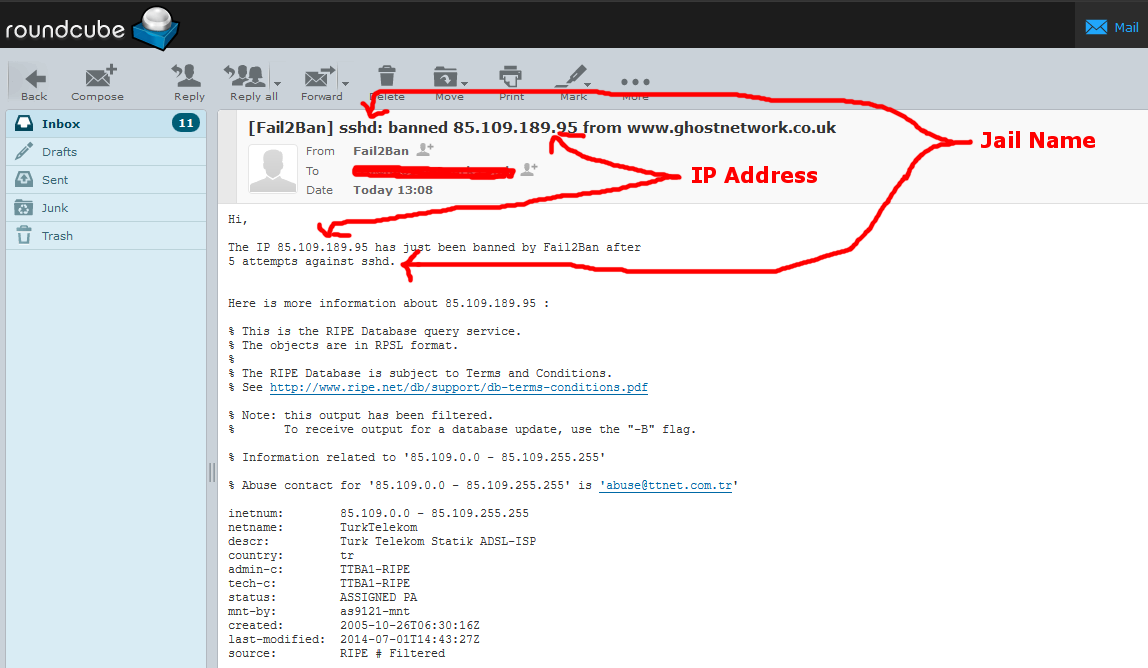
So in this example the IP address is 85.109.189.95, and the jail name sshd.
So to unban this one in Putty the command would be.
sudo fail2ban-client set sshd unbanip 85.109.189.95
As the basic command is
sudo fail2ban-client set JAIL-NAME unbanip IP-ADDRESS
So you would replace JAIL-NAME with sshd and IP-ADDRESS with 85.109.189.95 in our first example.
Hopefully you get the idea.
You can also get the information on who is banned from Putty, to do this first go into root user mode, using this command.
sudo su
Then issue this command.
Code: Select all
fail2ban-client status | grep "Jail list:" | sed "s/ //g" | awk '{split($2,a,",");for(i in a) system("fail2ban-client status " a[i])}' | grep "Status\|IP list"
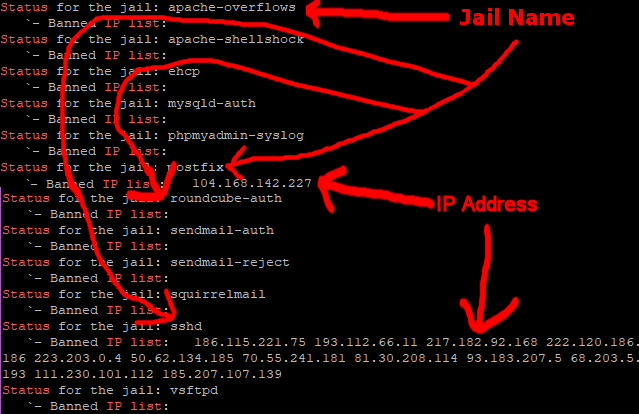
It’s always worth checking like this as I have known occasions, when I have not actually had an email about a ban.
After issuing this command come out of root user mode with this command.
exit
That’s it then, another job done.
NOTE: Please make sure you use the update script in THIS POST when updating EHCP force.